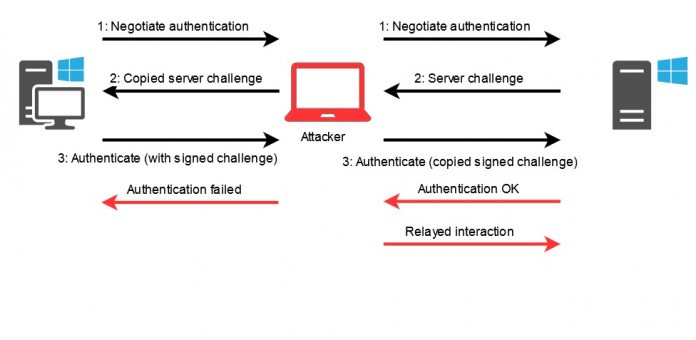
Dirk-jan Mollema, a security researcher for Fox-IT, says the zero-day is several vulnerabilities working together. He went public with the problem last week, describing three default settings that can be manipulated to increase access. Through a hacked lowly Microsoft Exchange email account, a bad actor can elevate account access to admin level. The Domain Controller is a secure server that handles authentication requests on Exchange. Mollema describes the following three vulnerabilities working in unison:
The default Exchange Web Services (EWS) feature gives attackers the ability to manipulate servers, allowing them to authenticate a bad actor through a hacked email account. To achieve this, the attacker uses NTLM hashes sent through HTTP, while the server will also not set Sign and Seal flags on the NTLM operation. Essentially, this means the NTLM authentication is left open to attack. Bad actors can then obtain the hash. Microsoft Exchange servers allow access to sensitive operations by default. Typically, only company admins have access to servers and the higher privileges, normal email account holders do not. However, with elevated access, the attackers can gain access to the Domain Controller and grant themselves access to sensitive material. Furthermore, the attack will allow the ability to create more backdoor accounts.
Solving Problems
PrivExchange works on Microsoft Exchange and Windows Server Domain Controllers from 2013 right up to fully patched versions. Microsoft has yet to officially discuss this vulnerability, so no patches are available yet. That said, Mollema has offered some workarounds for system admins to avoid being attacked.